Understanding Ransomware
You are here
Beware of the Ransomware VIRUSES
What is Ransomware?
It is the kind of virus that stops you from using your Computer, It holds your computer for a ransom.
According to Trend Micro a company that secures one's journey to the cloud, they say that this type of malware forces its victims to pay the ransom through certain online payment methods in order to grant access to their systems, or to get their data back. Some ransomware encrypts files (called Cryptolocker). Other ransomware use TOR to hide C&C communications (called CTB Locker).
They also say that the ransom prices vary, ranging from $USD 24 to more than $USD 600, or even its bitcoin equivalent. It is important to note, however, that paying for the ransom does not guarantee that users can eventually access the infected system.
It has been noted that ransomware can be downloaded by unwitting users by visiting malicious or compromised websites . It can also arrive as a payload, either dropped or downloaded by other malware. Some ransomware are delivered as attachments to spammed email.
Once executed in the system, a ransomware can either (1) lock the computer screen or (2) encrypt predetermined files with a password. In the first scenario, a ransomware shows a full-screen image or notification, which prevents victims from using their system. This also shows the instructions on how users can pay for the ransom. The second type of ransomware locks files like documents, spreadsheets and other important files.
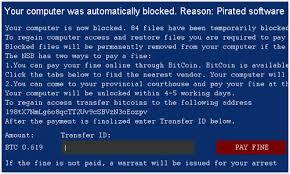
See Images of how the locked screen can be and what demand is put on the user of the computer

Image 1
That's how a locked computer looks like

Image 2
This is an example of the cryptolocker that one that encrypts files, folders, spreadsheets etc
According to the research done by Sophos, it says that there is also 'MBR ransomware'. The Master Boot Record (MBR) is a section of the computer's hard drive that allows the operating system to boot up. MBR ransomware changes the computer's MBR so the normal boot process is interrupted and a ransom demand is displayed on screen instead.
Because many of the users we have on our Makerere Network use Microsoft operating systems, they are the ones most susceptible to this type of attack.
DICTS encourages the use of the Universities Enterprise software solution which is Sophos, and your computer must be fully up to date because the writers of these virus programs keep updating. One of the good things about using an enterprise solution is that you can report the incident and a patch is released to enable us mitigate the problem.
What Can Be Done by I.T Administrator or a regular user?
This is our advice to System Administrators and the end users;
Advice to Systems Administrators
1. Backup your files regularly for servers- this can be done on an external hard drive or on the cloud (Google drive, drop box etc)
2. Prevent SPAM email from reaching end users.
3. educate users not to open any attachments that they are not expecting.
4. ensure local anti-virus is up to date on all computers and is active (ensure the user has not disabled the protection).
5. ensure your central shares (that endpoints update from) are receiving updates from Sophos Update Manager - check your console.
6. Report any suspicious activity to our helpme@dicts.mak.ac.ug
Advice to End Users
1. Backup your files regularly - this can be done on an external hard drive or on the cloud (Google drive, drop box etc)
2. Avoid opening any attachment emailed to you that you were not expecting.
3. Watch out for emails with attachments suggesting you must reply quickly or 'act fast' and hence feel compelled to open the attachment quickly - without considering the source.
4. Check your Sophos shield in the system tray and make sure it does not have a red cross or warning triangle.
5. Bookmark trusted websites and access these websites via bookmarks.
6. Scan your system regularly with anti-malware
7. Report any suspicious activity to our helpme@dicts.mak.ac.ug
A list of the latest Ransomware shall be provided.
For more visit this link http://www.makeuseof.com/tag/protect-data-ransomware-5-steps/
